Zero-Day Subscription
Exodus ensures that each and every discovered vulnerability is relevant, reliable, exploitable and well-documented before distributing to Exodus customers.
Enable Strategic Advantage
Mitigate Unknown Vulnerabilities for High-Profile Vendors
Exodus Intelligence discovers zero-day vulnerabilities that are unknown to the public and, possibly, the vendor. Our Vault contains thorough documentation of every vulnerability with detailed exploit analysis and mitigation guidance.
Commercial Vendors
- Microsoft
- Adobe
- EMC
- Novell
- IBM, and more
Industrial Control Systems Vendors
- Siemens
- GE
- Rockwell Automation, and more
Exodus Empowers Proactive Security

ACTIONABLE MITIGATION GUIDANCE
We provide in depth mitigation guidance as well as Snort or Yara rules to plug into existing defenses. Use the provided POC to test your implemented defenses.
DEFEND AGAINST THE UNKNOWN
We utilize expert reverse engineering and vulnerability research to “detect the undetectable” and help our customers thwart malicious cyber adversaries.
EXCLUSIVE ACCESS & PREVENTION
Exodus utilizes advanced proprietary reverse engineering tools, tactics, and techniques to discover, exploit, and deliver unknown vulnerability details to subscribing customers.
The Exodus Intelligence Vault
Our subscribers can access our library of vulnerability research through The Vault. Each Vulnerability Intelligence Package contains thorough documentation of the vulnerability with detailed exploit analysis and mitigation guidance.
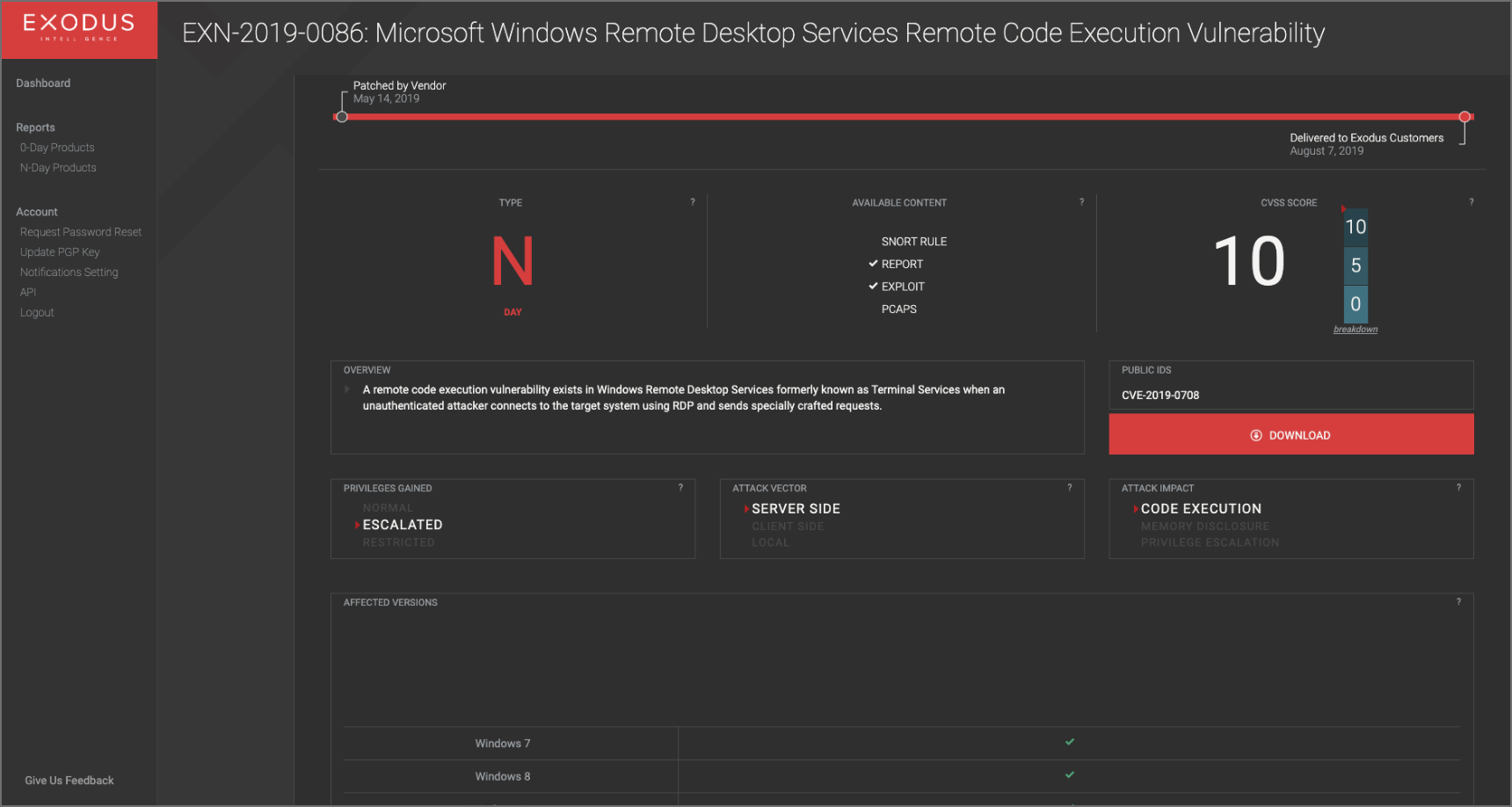
The Vault was designed to prioritize decision-driving information in an easily navigable interface. Users can assess the criticality of the Vulnerability at a glance by reviewing:
- Vulnerability Timeline
- CVSS Score
- Privileges Gained
- Attack Vector
- Attack Impact
- Affected Versions
Vulnerability Intelligence Packages
Exodus offers actionable intelligence that will allow you to test and optimize your defense, with precision. Every vulnerability is well documented and filed securely in the Exodus Vault. Our Vulnerability Intelligence Packages include:
Vulnerability Intelligence Report
Understand all aspects of the vulnerability
XML File
Integrate defenses into third-party detection, prevention and security integration products
Proof of Concept
Test your defenses with provided POCs
Network Packet Captures
See examples of both malicious and benign traffic
A Closer Look at the Vulnerability Intelligence Report
The written report is 15 to 30 pages covering all aspects of the vulnerability, including:
- Affected products, versions, supported architectures, and hashes of binary files
- Target market share, common usage, and typical deployment configurations
- Technical information on the vulnerable components and enumeration of attack vectors
- Disassembly and/or source code walkthroughs showing the flaw in the code
- Detailed information on attack vectors and corresponding malicious network traffic
- An explanation of the required exploitation process, including bypassing mitigations
- Guidance on how to detect an attack in progress, as well as artifacts left behind in the case of a successful compromise
- Insight into the requirements, reliability, difficulty, and likelihood of an attacker successfully exploiting the issue
- Guidance on reducing or eliminating susceptibility to the flaw in place of an official patch from the affected vendor